One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Scott – N8SY and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Scott has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the section will need to use the mailing list link above.
Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
Go to www.arrl.org and logon.
Click Edit your Profile.
You will be taken to the Edit Your Profile page. On the first tab Edit Info, verify your Email address is correct.
Click the Edit Email Subscriptions tab.
Check the News and information from your Division Director and Section Manager box.
Click Save.
Now without further ado…
Read the full edition at:
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
As the Technical Coordinator for the Ohio Section, I’m responsible for the Technical Specialists. The Specialists and I are here to promote technical advances and experimentation in the hobby. We encourage amateurs in the section to share their technical achievements with others in QST, at club meetings, in club newsletters, hamfests, and conventions. We’re available to assist program committees in finding or providing suitable programs for local club meetings, ARRL hamfests, and conventions in the section. When called upon, serve as advisors in issues of RFI and work with ARRL officials and appointees for technical advice.
The Technical Specialists really make all this happen. In the Ohio Section, there are about 15 qualified and competent Specialists willing to help. They meet the obligation of advancing the radio art bestowed to us by the FCC. The TSes support the Section in two main areas of responsibility: Radio Frequency Interference and technical information. RFI can include harmful interference that seriously degrades, obstructs, or repeatedly interrupts a radiocommunication service. Ranging from bad insulators on telephone poles to grow lights and poorly made transformers, they can help with RFI direction finding or assist in locating bozo stations. Technical information is everything else from building antennas, repeaters and controllers, digital, computers, networking, and embedded devices.
How can we help? The knowledge and abilities of your Technical Specialists are quite impressive. Here are some examples of the knowledge the Technical Specialists provide:
- Documentation and training
- VHF/UHF portable operation
- Antennas (fixed, portable, and mobile)
- Batteries and emergency power
- Experts in RFI from powerline and consumer devices
- VHF/UHF/SHF contesting
- Experts in test equipment
- Automotive electronic compatibility (EMC) and interference (EMI)
- Repeaters
- Digital modes (D-STAR, DMR, Fusion, P25, APRS & IGates. HF: MT63, FT8/4, Olivia, PSK).
- Computers and networking (VoIP – AllStar link, software engineering, embedded systems – Raspberry Pi, Arduino)
- Society of Broadcast Engineers (SBE) members knowledgeable in interference problems
This impressive list of qualifications is available to all in the Ohio Section. Looking for help in one of these areas? Need a program for your club? How about a technical talk or forum at your hamfest? Feel free to contact myself. My contact info is near my picture and on the arrl-ohio.org website. I’ll assist getting you in touch with an appropriate Technical Specialist. One of the Specialists might hear a plea for help and reach out to you as well.
Where have all the maps gone?
A lot of ham radio is about location and maps – APRS, repeater locations, grid square, propagation, beacons, satellite, or spotting maps. You may have noticed, starting last year, the quality of maps has degraded or looked different on your favorite website or on your favorite app. You’re not going crazy. It’s because many of those who developed their map around Google Maps API were forced to make some changes and decisions.
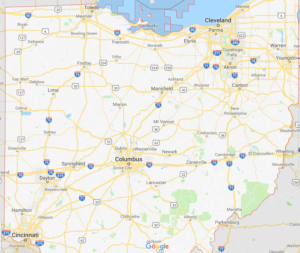
If you’re not a programmer, an API stands for Application Programming Interface. APIs are a set of defined tools or commands that can be called allowing for easy communication between different components or systems. If an API is available, they are (supposed to be) well documented and available for anyone to use.
Since the Google Maps service existed, it could be used for free. There were usage limits but they were artificially high enough were most implementations we not going to hit 25,000 requests/day. If requests exceeded the daily limit, the owner was charged $0.50/additional 1,000 requests up to 100,000 in a 24-hour period. If that maximum was reached per day, it was likely a heavy traffic website and commercial in nature where overages could be supplemented.
Last year, Google reduced the number of free requests to 28,000/month, which is the $200 “credit” referred to in their pricing plan. Additionally, it was required of the developer to register for an API key. That key MUST be linked to a credit card even if usage didn’t come anywhere near the free credit. Overages are automatically charged to the linked credit card and amount to $7.00 per 1,000 additional requests.
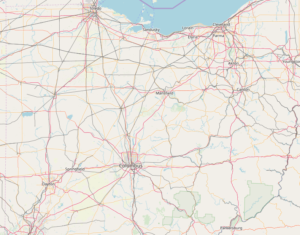
It still sounds like a lot of requests per month, but not when I think about sites I have running in the shack. I can easily refresh sites 10 times while I’m operating. If 2,800 other hams did the same thing, all of a sudden, they’ve blown through their free credit. This put many free and non-profit developers between a rock and a hard place. Start shelling out for hefty overage fees for access to Google Maps – which was arguably very good, move to an alternative, or close shop. Commercial sites, which sell products and services or rely on ad revenue, have stayed with Google Maps because they can offset that cost with subscriptions or ads. Free, non-profit, and programmers doing it for fun have moved to a free and open license alternative called OpenStreetMap. I came across one website that said, “I’m done” citing the price hike and closed their site.
These microservices are provided free (as in beer). They end up not being able to monetize the service so they drastically change it or its pricing. This is happening quite often in tech and will continue as we rely more and more on other services.
100 Points at Field Day!
The next big ham holiday, Field Day, is right around the corner! Get out and join your club or find a club to join if you’re not a member of one. It’s a great time to bring friends or hams that have been out of the hobby excited about ham radio. Hams that come out get bitten by the bug to expand their station or learn a new mode. Check the Field Day Locator for operations taking place near you.
Sending 10 messages over RF from your site gets you 100 points – including Winlink messages. I love to receive messages about your setup, stations, operating, or social activities taking place. These can be sent via the National Traffic System (NTS) or Winlink – K8JTK at Winlink.org – to my station. I haven’t seen the usual post on the Winlink site of other stations willing to receive messages from Field Day stations as in the past.
With July around the corner, if you’re looking to do something while flipping burgers at your 4th of July picnic, my favorite event 13 Colonies Special Event will be on the air July 1 – 7.
Thanks for reading and 73… de Jeff – K8JTK