One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Tom – WB8LCD and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Tom has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the Ohio section will need to use the mailing list link above. Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
- Go to www.arrl.org and click the Login button.
- Login
- When logged in successfully, it will say “Hello <Name>” in place of the Login button where <Name> is your name. Click your Name. This will take you to the “My Account” page.
- On the left hand side, under the “Communication” heading (second from the bottom), click Opt In/Out
- To the right of the “Opt In/Out” heading, click Edit
- Check the box next to “Division and Section News.” If it is already checked, you are already receiving the Ohio Section Journal.
- Click Save
- There should now be a green check mark next to “Division and Section News.” You’re all set!
Now without further ado…
Read the full edition at:
- https://arrl-ohio.org/news/2024/OSJ-June-2024.pdf
- https://arrl-ohio.org/news/2024/OSJ-June-2024.docx
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
As Technical Coordinator for the Ohio Section, I oversee the section’s Technical Specialists. We are here to promote technical advances and the experimentation side of the hobby by encouraging amateurs in the section to share their technical achievements in QST, at club meetings, in club newsletters, and at hamfests and conventions. We are available to assist program committees in finding or providing suitable programs for local club meetings, ARRL hamfests, and conventions within the section. When called upon, serve as advisors for RFI issues and work with ARRL officials and other appointees providing technical advice.
Technical Specialists are a cadre of qualified and competent individuals here for the “advancement of the radio art,” a profound obligation incurred under the rules of the FCC. TS’s support myself and the section in two main areas of responsibility: Radio Frequency Interference (RFI) and technical information. They can specialize in one or more areas or be generalists with knowledge in many areas. Responsibilities range from serving as consultants or advisors to local hams or speaking at local club meetings on popular topics. In the Ohio Section, there are 12 qualified specialists.
RFI and EMI (electromagnetic interference) includes harmful interference that seriously degrades, obstructs, or repeatedly interrupts a radio communication service such as ham radio or public service agencies. RFI sources range from bad power insulators, industrial control systems, nearby or poorly made transmitters, household appliances, personal devices like computers, monitors, printers, game consoles – to grow lights, failing or poorly made transformers, and devices hams brag about getting cheap from China. Technical Specialists can offer advice to help track down interference or locate bozo stations when called upon. Technical information is wide-ranging, everything from antennas to Zumspots.
How can we help? The knowledge and abilities of YOUR Technical Specialists are really quite impressive:
- Amplifiers
- Antennas (fixed, portable, emergency operation)
- Antenna systems such as towers, guying, coax/feedlines, and baluns
- Boat anchors (tube technology)
- Computer systems – Windows, Linux, Raspberry Pi
- Digital voice and data modes – including D-STAR, DMR, Fusion, NXDN, P25, APRS, IGates, packet, TNCs, MT63, FT8/4, Olivia, PSK, etc.
- Direction finding
- Electronics and circuits, including teachers whom have taught electronics classes
- Former repair technicians
- Home brew
- Internet linking (Voice over IP, aka VoIP) – Echolink, AllStar/HamVoIP, DVSwitch, PBX/Asterisk
- Mobile installations – HF, VHF/UHF, antennas
- Narrow Band Emergency Messaging System (NBEMS) – Fldigi and Flmsg
- Networking – AMPRNet, routers, port forwarding, ISPs, firewalls, mesh, microwave
- Power supplies
- Propagation
- Repeaters, controllers, and high-profile systems
- RFI caused by power lines and consumer appliances
- RF safety
- SHARES stations (SHAred RESources – Department of Homeland Security HF radio program)
- Software Defined Radios (SDR)
- Tower safety
- Professional certifications such as Motorola Certified Technicians, Master Electrician, Certified Journeyman Electronics Technician, General Radiotelephone Operator License (GROL), ETA certifications, Society of Broadcast Engineers (SBE) certifications and affiliations, and Marine Radio Operator permit holders.
This impressive list of qualifications are available resources to all in the Ohio Section. Looking for guidance in one of these areas? Need a program for your club meeting? How about a technical talk or forum at a hamfest? Assistance or direction on a project? My contact info is near my picture and on the arrl-ohio.org website. I’ll assist getting you in touch with an appropriate Technical Specialist.
Hamvetion Recap

Another Hamvention has come and gone. This was emotional because this was the first since my dad passed, N8ETP. Hamvention was something we did together. He didn’t go last year because (we didn’t know it at the time) he was suffering from post-operation complications. He was looking out from above because I had no shortage of company on this trip. I checked into the hotel, then went to dinner. Immediately met a father and son on their first trip to Hamvention. We talked about the show, past shows, what to expect, and some pro tips. Ironically, the dad was released from the hospital a week prior after recovering from an infection. If they’re reading, I apologize I don’t remember your calls – send me a message and I’ll add them later.
Figuring the rain would keep attendees away Friday morning, traffic was worse than anticipated. Busses were stuck in with those trying to get into on-site parking, causing delays and lines at the high school. It took over an hour from the high school until I got into the fairgrounds. Broke out the poncho for the first time in a number of years.
After being admitted, checked in with the ARRL Ohio Section/Great Lakes Division table to say howdy to our leadership and swap stories. Shortly after leaving the booth, ran into George – W5JDX and Mike – VE3MIC from AmateurLogic.TV and spent the rest of the day hanging out with those guys. Due to rain, George didn’t do any recording until after we grabbed some lunch. Hilarity insured behind the camera as well as in front.
I left about 4pm to get ready for dinner. At dinner, I ran into George again. We were chatting and before we knew it, realized it was 8pm. We had intended on going to the D-STAR evening gathering but didn’t make it since we were having a big time.
Saturday, ran into Mike – this time in the flea market – and we walked a good portion of it in the morning. Mike and cousin Jerry were going to head back home around noon. I walked the rest of the flea market because that was something dad liked to do too. Before leaving, talked with some inside vendors I wanted to speak to.

Shopping list was sparse this year. Only thing I was really looking out for was a place that built ham shacks/outdoor buildings. The camper converted into my existing hamshack really needs to be replaced. I didn’t see any builders there. Rest of the shopping list was “nice to haves” – radio with a TNC for APRS or Winlink. Maybe other APRS gear. Couple Motorola pieces of equipment I’ve been looking for. Been wanting to get a D-STAR radio with the latest features. I took advantage of a show special at DX Engineering and picked up an ICOM ID-52, mainly because the restrictions (by ICOM) were lifted on the show specials.
A ham in the area, whom I’ve gotten to know, was looking to unload some of his gear. I picked up a used ICOM IC-746Pro and Micro Keyer. Fortunately, I was able to try out the radio before I bought it. Doing some research online found out the most common problems with the 746 are the display backlight goes flaky, eventually crapps out, and a dead transmitter. Both were non-issues.
This ham did say the tuning knob might be loose. It didn’t seem much different than my IC-7000. Upon using it at home, there might be an issue with the knob because it does repeat the same frequency numbers over and over again on occasion. I’ll look into tightening or cleaning the knob/encoder to see if that resolves it. It’s not a big deal because most of my operation is digital and I use remote control through a CI-V cable.
Otherwise, it’s been working fine on Winlink. There are a couple differences I like in my 7000 over the 746. Main one being it keeps switching back to USB from D-USB for digital operation. Functionally, it’s working as expected.
A stop at Micro Center in Columbus on the trip back home is required for some post-Hamvention spending. The Columbus location is a bigger store than my closest location on the east side of Cleveland (Mayfield Heights), which means they have more stuff out on display. I needed some larger capacity USB Flash Drives and they had a Lenovo ThinkPad on sale. I’d been having trouble with my existing laptop failing to charge the battery. I found out the Columbus store is a larger location because it is the flagship store for Micro Center as their headquarters are about 15 minutes away. That store will have items not (yet) available at other locations as a test to see if an item sells out.
The same general themes kept popping up before the show and at the show from other attendees: ‘this maybe [my] last one’ and ‘show specials can be found online.’ With the economy in the crapper and inflation in its current state, it’s getting even more expensive to attend Hamvention. $500 and up for a single room in the area for the weekend. With other local events, such as grade school sporting tournaments and antique flea markets, hotel rates are higher due to demand. There were a couple issues at my hotel too. While the staff tried to make it right offering bonus points, the issues still shouldn’t have happened when you’re paying that much for a room. An inconvenience for what was supposed to be an otherwise enjoyable time.
Hamvention show specials, for the most part, can be found online too. Not all distributors bring a lot of gear (inventory) to sell – except for maybe the most popular radios and models. Heil Sound is one vendor most people I know reference because we were involved with Ham Nation. Back at Hara Arena, they had an entire side of Audio Alley with equipment and inventory for sale. Heil Sound had a 6-foot table this year showcasing headset and some microphone offerings. They, like many others, are relying on distributors for show specials and handling of inventory – which goes back to the show specials are also found online. MFJ wasn’t there because they ceased production as the show was getting underway. I heard in the flea market: ‘sellers are looking for top dollar and buyers are looking for the cheapest deals.’ Things weren’t flying out of the flea market either.
Despite that, according to the Hamvention website, this year’s event was record-setting attendance at 35,877. I will always be of the belief “if you’ve never been to Hamvention, you need to go at least once in your life.” It’s more of a social and nightlife gathering, with vendors putting new gear ‘under glass’ at the show.
ARRL Network Incident
Not to bury the lead but I figure I would touch on the announcement posted on the ARRL website regarding the “serious incident involving access to our network and headquarters-based systems.” This incident was big enough news to make an online Cybersecurity trade publication, SecurityWeek. I don’t know anything more than the information made available in the league’s post but I suspect the last paragraph in the SecurityWeek article is the reason.
From the Information Security side, in this day and age, where everyone wants things to be convenient – conveniently accessible resources, conveniently ways to order things online, convenient ways to make membership changes, convenient apps to use – it’s not a matter of “if” something will be compromised, but “when” will something be compromised. The “when” for the ARRL happened to be right before Hamvention.
As noted in the ARRL post, people are asking if personal information is compromised – they haven’t said “yes” but it seems very likely. How an organization comes out looking in these trying times comes down to how they handle their responses – how they improve security posture, how they communicate the extent of the breach to its members, reporting to regulators/investigators, services offered to those concerned about their personal information, how they clean up and recover, making sure it doesn’t happen again, etc. If true, the “ARRL does not store credit card information anywhere on our systems, and we do not collect social security numbers” which helps with regulators and government but leaves privacy minded individuals who do not wish for personal details, albeit “publicly available,” to fall into the wrong hands.
Yes, this absolutely should not have happened. In a perfect world, it wouldn’t have happened. We don’t live in a perfect world and not everyone is perfect despite how some present themselves.
From my own experience, working with vendors and Managed Service Providers (MSPs), it takes a lot of extra work to make sure what they are telling you is correct and make sure what they do is correct. ARRL does use Microsoft services and they’ve had their share of scathing reports of inadequate security practices recently. I work with a lot of different Information Technology (IT) teams. The number of analysts (and management) that know very technical details about systems they are responsible – is remarkably low. When an analyst doesn’t know their system, doesn’t know how modifications affect that system, how would they know if a modification opens their organization to attack? Maybe an employee was thinking they were doing their job but clicked a password stealing link or downloaded a fake invoice containing a malicious payload (malware that performs malicious activity). The latter is often due to a lack of proper training in security practices for general employees. Again, these are only my experiences and observations working in IT.
The ARRL posting has been updated several times as recovery progresses and systems come back online. This disrupted most ARRL IT systems including phone systems, Logbook of the World (LoTW), VEC application processing, some magazine resources, store orders and shipping. LoTW data is “secure” presumably meaning no uploaded contact logs have been lost. The arrl.net forwarding system was not affected but I’ve been moving off it due to messages being bounced previously.
Thanks for reading and 73… de Jeff – K8JTK










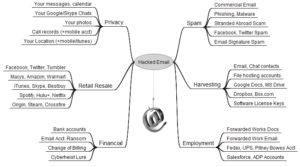
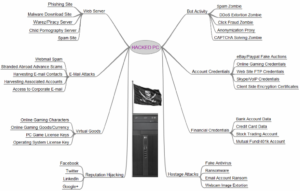

 Back to Fldigi. The developer of Fldigi maintained the installer and source files on his own server. Somewhere near the end of last year, his site was hacked. The decision was made to move the files from his server over to SourceForge. Likely in an attempt to be more secure.
Back to Fldigi. The developer of Fldigi maintained the installer and source files on his own server. Somewhere near the end of last year, his site was hacked. The decision was made to move the files from his server over to SourceForge. Likely in an attempt to be more secure.