One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Tom – WB8LCD and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Tom has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the Ohio section will need to use the mailing list link above. Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
- Go to www.arrl.org and click the Login button.
- Login
- When logged in successfully, it will say “Hello <Name>” in place of the Login button where <Name> is your name. Click your Name. This will take you to the “My Account” page.
- On the left hand side, under the “Communication” heading (second from the bottom), click Opt In/Out
- To the right of the “Opt In/Out” heading, click Edit
- Check the box next to “Division and Section News.” If it is already checked, you are already receiving the Ohio Section Journal.
- Click Save
- There should now be a green check mark next to “Division and Section News.” You’re all set!
Now without further ado…
Read the full edition at:
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
Two years ago, I wrote an article for the OSJ dealing with “cyber hygiene” – practices and precautions users take to keep their data safe and secure from outside attacks. I didn’t rehash it last October since most of the article was still relevant. For this year’s “Cyber Security Month,” it’s time for an update. I still encourage everyone to re-read that article in the October 2020 OSJ or on my website as 95% of it is still best-practice for normal people.
The browser is still one of the most utilized pieces of software in modern computing and one of the most attacked. Users hanging on to Internet Explorer are finding it harder and harder to visit modern sites as new encryption standards are recognized and made industry standard. Using an End of Life browser, users are seeing a lot of “This page can’t be displayed” because it doesn’t support current methods of protecting communication.
Chrome, Firefox, Microsoft Edge, and Opera remain good choices. Brave browser is a good alternative if you don’t want to use a native Google browser. It’s based on the Chromium project for those who want a privacy-focused browser. Before jumping to Brave, some things to be aware of before you have a jarring first impression. There are ads – mostly for cryptocurrency. Why recommend an ad supported browser for crypto-what? Unlike Chrome, which makes money on user’s data, Brave pays the bills with safe ads (opposed to malicious ones that would infect your computer). They can be turned off. If ads in a browser are not your cup of tea, there are plenty of other browser options but note Brave took top spot for privacy in terms of phoning home:
Used "out of the box" with its default settings Brave is by far the most private of the browsers studied. We did not find any use of identifiers allowing tracking of IP address over time, and no sharing of the details of web pages visited with backend servers (Leith).
Pi-Hole and 3rd party DNS services, such as Quad 9, are good options for blocking ads, tracking, annoyances, and malicious content at the network level. To go a step further and block unwanted social media, games, messaging apps, dating sites, or streaming services or entire categories of sites, freemium services like NextDNS and AdGuard offer additional blocking options. Advanced features including newly registered domain blocking, typo-squatting domain blocking (domains registered by squatters taking advantage of type-o’s made when users are inputting a site’s URL), parked domains, and entire top-level domain blocking go above Pi-Hole and other free services.
Free tier gives you a limited number of DNS queries. With devices that freak out when they can’t phone home or heck, the cloud providers used by my workplace, you’ll blow through the free tier quickly. With a yearly plan, the price is around $1.75/month. OpenDNS has a completely free tier with basic blocking. Their blocking of services and categories is also a premium option.
Note devices with hard coded or manually entered DNS for other services (such as the popular Google DNS 8.8.8.8) will bypass these protections. A router/firewall with the ability to intercept and re-direct traffic (also called internal port-forward or inside NAT) will stop requests from reaching other DNS services and redirect them to the service of choice.
LastPass, in 2021, decided to make their free tier limited to a device of a single type. Mobile or desktop, not both. To sync between both, a premium account was needed. Granted $3/month isn’t a huge amount (you can give up one coffee), users opted for a service called Bitwarden. It is an open-source password manager offering unlimited devices for free and a family account for $3.33/month with unlimited sharing. An option that appeals to me is the self-hosted option where you are in-control of your data.
KeePass remains a strong choice for managing password databases, especially offline. I recently moved to a fork called KeePassXC. Its lineage came from KeePass in that KeePassX was a fork of KeePass, KeePassXC is a fork of KeePassX. It too is free, open source, and databases are compatible between KeePass and XC if you want to try or use both. I like KeePassXC better due to its cross-platform support and TOTP/2FA integration.
Beyond my 2020 article, I would like to address the issue of administering devices remotely. In particular, devices we leave at remote sites or have in “the cloud.” Whether that is an AllStar node, EchoLink/SVX, Wires-X, router, controller, mesh node, or digital mode reflector. Though I’m writing this in the context of ham radio devices, this applies to anything – including devices on home networks. I hate the idea of devices, which provide services to a very small group, being available to anyone on the Internet. It’s dumb, terrible security practice, hygiene, and there are better options.
‘Well, my device is password protected!’ Most don’t change the default password on their device. Ones that do many have purchased from a dud company that ignores vulnerabilities for 3 years that, in theory, would allow anyone access to their camera, Wyze.
For clarification, I’m not taking the ports needed for normal user access to the AllStar/Wires-X/EchoLink/reflector/whatever. I’m specifically talking about the ports needed for administrative access. Ones such as SSH and remote desktop. Admins that figured out OpenVPN or WireGuard tunnels or ones that only have local access to admin services, you’re good.
With common admin services open to the Internet, check the logs. Internet miscreants are trying common username and password combinations. Not to mention probes not seen in logs like fingerprinting to figure out which outdated version is running and looking up exploits against that version. Once they get in, they will configure that device to be a cryptocurrency miner (making money for the bad guy), another device in their bot army used for attacking other victims, figuring what other devices they can get into, not to mention backdoors allowing them access at any time. When this happens, that device can no longer be trusted.
Fail2Ban is a popular option that only slows down attackers, doesn’t provide distributed brute-force attack protection, and is not available on Windows. Doesn’t solve the issue of unnecessarily exposing admin services to the Internet. Changing ports is not secure, often called security through obscurity – which is not security. A quick scan of the IP address will reveal the new port. SSH keys with PasswordAuthentication set to “no” is about as good of protection as you can get when wide-open access is needed.
ZeroTier and Talescale are an easy-to-use middle ground between the options of wide-open access and creating your own VPN connections. Both services create secure connections to just about any device including: Windows, MacOS, Android, iOS, Linux (including Raspberry Pi), BSD, and some Network Attached Storage devices. The device reaches out to a central server or peer, establishing a private connection. Permitted users are then able to establish connections with that device. A club might have five administrators, all five would have provisioned accounts for access to their club’s remote site devices.
These services are freemium and proprietary (not open-source) but they do have self-hosted options. Once the service is up and running, close the administration service ports in the router. Configure the device to only accept connections for admin services on the ZeroTier or Talescale interfaces.
For web services, such as status pages or dashboards running on devices at remote sites, something to consider is a reverse proxy as an additional layer of protection. Normally: install and configure the device with a web server stack, install a dashboard or status page, port forward 80 & 443, then hand out an IP address to users or provide link on the club’s webpage to that device, maybe using a DNS/dynamic DNS entry. You’re off and running. The device remains exposed to the Internet. Miscreants could send random junk attempting to bypass authentication or flood the connection with bogus data, denying legitimate users’ access (denial of service).
A reverse proxy works by being the point at which users access the site. Cloudflare is one such reverse proxy service and offers a free tier for personal/hobby sites. The proxy inspects traffic to determine if it is legitimate. Legitimate traffic is allowed to pass onto the server. Illegitimate traffic is dropped and never seen by the server, protecting it from possible malicious traffic. An additional benefit is the real IP address of the server or device, at a site or at home, is not easily determined, making the device less unlikely to be exploited.
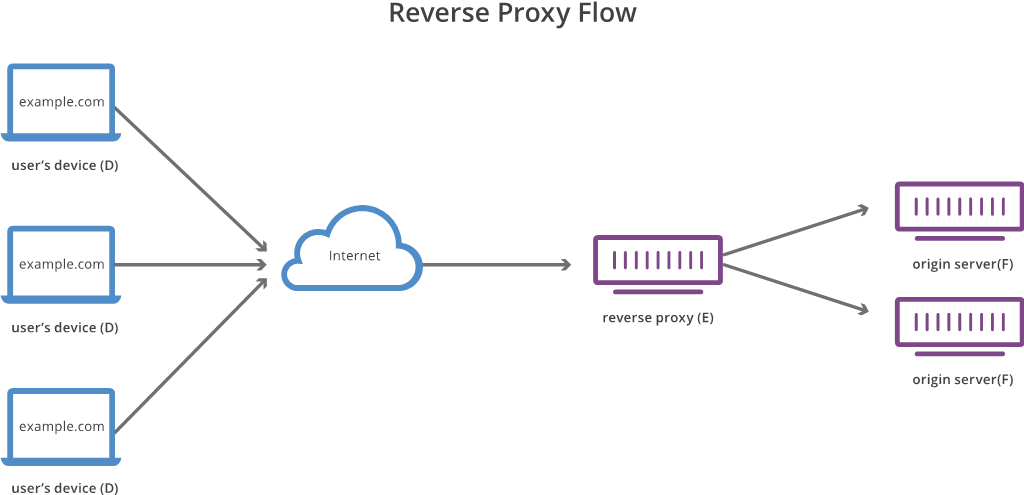
This protects the device in a different way from that of a private link or VPN like ZeroTier or OpenVPN. The web site is still accessible to anyone on the internet. Having visitor’s setup private links or VPNs for commonly accessible web services is not practical and not something a majority of users will not opt into freely.
The Cuyahoga Amateur Radio Society (CARS) asked for one of our technical presentations at their meeting on October 11th. I was able to give a presentation put together by Technical Specialist, Bob – K8MD, on DMR. He was out-of-town but I was able to give his presentation. There was plenty of questions and good discussion after the presentation. I brought one of my hotspots and a DMR radio to demonstrate the AmateurLogic.TV Sound Check Net on my multimode system. The net got started about when the meeting wrapped up which was perfect timing. If your club is interested in this or another technical topic, let me know!
I heard from many hams that found my Hamshack Hotline tip useful in last month’s OSJ, including ones outside our section. Yes, they are reading THE OHIO Section Journal =) Some updates: even long after the DNS entry was removed, phones apparently cached the IP address. Some reported their phone still had green lights though the admin interface contained the old DNS entry. With this information, the phone will likely remain working until rebooted. Additionally, as suspected, other domains were seen. Replacing hhux.wizworks.net with hhux.hamshackhotline.com also worked. Some replaced the entire string with only hamshackhotline.com, leaving off subdomains like hhus (as was shown) or hhux. This won’t work either. The subdomain must remain intact.
Thanks for reading and 73… de Jeff – K8JTK
