One of the responsibilities of the Technical Coordinator in the Ohio Section is to submit something for the Section Journal. The Section Journal covers Amateur Radio related things happening in and around the ARRL Ohio Section. It is published by the Section Manager Scott – N8SY and articles are submitted by cabinet members.
Once my article is published in the Journal, I will also make it available on my site with a link to the published edition.
You can receive the Journal and other Ohio Section news by joining the mailing list Scott has setup. You do not need to be a member of the ARRL, Ohio Section, or even a ham to join the mailing list. Please sign up!
If you are an ARRL member and reside in the Ohio Section, update your mailing preferences to receive Ohio Section news in your inbox. Those residing outside the section will need to use the mailing list link above.
Updating your ARRL profile will deliver news from the section where you reside (if the leadership chooses to use this method).
Go to www.arrl.org and logon.
Click Edit your Profile.
You will be taken to the Edit Your Profile page. On the first tab Edit Info, verify your Email address is correct.
Click the Edit Email Subscriptions tab.
Check the News and information from your Division Director and Section Manager box.
Click Save.
Now without further ado…
Read the full edition at: http://n8sy2.blogspot.com/2016/12/december-edition-of-ohio-section-journal.html
THE TECHNICAL COORDINATOR
Jeff Kopcak – TC
k8jtk@arrl.net
In October, I was invited by Medina County ARES to see a presentation about Winlink. I had heard of it as a way to send email messages over the HF bands. There were rumors around whether specialized hardware was needed and I really wanted to see what it was all about. Rick – K8CAV gave a great presentation on how it all works and some tips that really helped me get operating on Winlink.
 Winlink, in short, is a way to send email via radio circuits frequently used by RV campers, boaters, and mariners where the Internet may not be available or reliable. It is a store and forward system meaning your messages will be held and delivered when you call into a gateway, much like the dial-up or BBS days. There are a number of ways the software will operate: connect to a remote gateway station over the air, operate peer-to-peer over-the-air, connect via the Internet using Telnet (yeah, yeah ‘telnet isn’t secure’ but neither is your email going out over the air), or webmail. Winlink has regional Central Messaging Servers (CMS) which connect to the Radio Messaging Servers (RMS) over the Internet. The RMS is the gateway your client connects to for sending and receiving messages over-the-air.
Winlink, in short, is a way to send email via radio circuits frequently used by RV campers, boaters, and mariners where the Internet may not be available or reliable. It is a store and forward system meaning your messages will be held and delivered when you call into a gateway, much like the dial-up or BBS days. There are a number of ways the software will operate: connect to a remote gateway station over the air, operate peer-to-peer over-the-air, connect via the Internet using Telnet (yeah, yeah ‘telnet isn’t secure’ but neither is your email going out over the air), or webmail. Winlink has regional Central Messaging Servers (CMS) which connect to the Radio Messaging Servers (RMS) over the Internet. The RMS is the gateway your client connects to for sending and receiving messages over-the-air.
There is little privacy as other stations can read your messages but the intent is to have a worldwide emergency email messaging system. Messages can be exchanged with any email address (Gmail, your ISP) on the Internet using the assigned callsign@winlink.org email address. Stations conducting business will likely get blocked from the RMS gateways. Attachments can be included with messages but due to bandwidth, these should be kept to small files like CSV or TXT files – no multi-megapixel images or videos.
There are three pieces to the Winlink client software: RMS Express is the ’90’s looking email client, Winmor – the modem, and ITS HF Propagation is a third party software program that works with Winmor to determine propagation for connection reliability. I got Winlink setup and working with my radio and SignaLink so no specialized hardware is required. A lot of back-and-forth transmit and receiving happens between the client and gateway. The TX/RX turn-around time needs to happen quickly (under 200ms), longer will require a high number of retransmissions. One tip to help minimize the delay: set the SignaLink delay control no further than the second hash mark (8 o’clock position). To get started, go to ftp://autoupdate.winlink.org. Click “User Programs.” Download and install “Winlink Express Install,” and “itshfbc” to their default locations. To get an account created on the system, you need to send one email to an Internet address such as your personal email. In addition, Winlink has an “APRSLink” where you can check for messages, read, compose, forward, and delete all by sending APRS messages. Feel free to send me a message to “my call” at winlink.org. More: http://www.winlink.org/
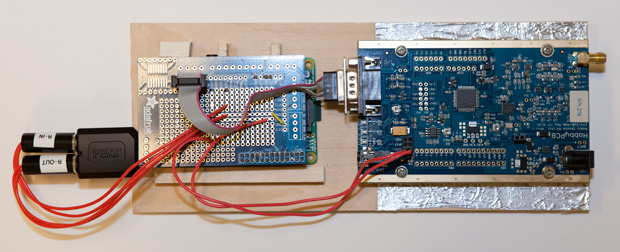
 I’ve also been playing around with a new device from Shark RF called the OpenSpot. It’s a small company with two guys in Estonia (South of Finland). Production is done on a batching basis so there is a waiting list. It seems like they’re shipping units close to once per month. Once I got the shipping notice, I had the device within a week. They say 3-6 business days shipping time and it arrived certainly within that range. The OpenSpot is a standalone digital radio gateway otherwise known as a hotspot. It currently supports DMR (Brandmeister, DMR+), D-STAR (DPlus/REF, DCS, XRF/DExtra, XLX), and System Fusion (FCS, YSFReflector). If the mode or network isn’t supported, they do take requests and will make additions available via firmware upgrades. Since it is a hotspot device a transceiver capable of operating that mode is required. They are doing something cool since DMR and Fusion use the AMBE2 codec. A DMR radio can be used to access the Fusion network and vice-versa (DMR Talk Groups with a Fusion radio).
I’ve also been playing around with a new device from Shark RF called the OpenSpot. It’s a small company with two guys in Estonia (South of Finland). Production is done on a batching basis so there is a waiting list. It seems like they’re shipping units close to once per month. Once I got the shipping notice, I had the device within a week. They say 3-6 business days shipping time and it arrived certainly within that range. The OpenSpot is a standalone digital radio gateway otherwise known as a hotspot. It currently supports DMR (Brandmeister, DMR+), D-STAR (DPlus/REF, DCS, XRF/DExtra, XLX), and System Fusion (FCS, YSFReflector). If the mode or network isn’t supported, they do take requests and will make additions available via firmware upgrades. Since it is a hotspot device a transceiver capable of operating that mode is required. They are doing something cool since DMR and Fusion use the AMBE2 codec. A DMR radio can be used to access the Fusion network and vice-versa (DMR Talk Groups with a Fusion radio).
The OpenSpot has a lot of flexibility, very well designed, and is superior to the DV4Mini. It doesn’t need different Raspberry Pi images for different modes like the DVMega. The device comes with everything: the OpenSpot hotspot, Ethernet cable, USB cable, USB power adapter, and antenna. It runs an internal webserver for device configuration. I even like how they do the firmware update process. The OpenSpot shows up as a drive to the computer and using the copy command – copy the firmware to it and voilà – done. For DMR, it will operate like a DV4Mini with the radio configured in TG 9 (talk-group) or it will operate like a repeater (my preference) where the Talk Groups are push-to-talk. All the TAC groups are available (310, 311, 312, etc) and call routing works. I could not get these to go on the DV4Mini. D-STAR works great too. You can link and unlink to reflectors using radio commands. It does not have a drop down for linking directly to a D-STAR repeater on the network. The only systems listed are reflectors. Forum posts describe how to link to a D-STAR repeater (like a DVAP or DNGL would do) using the “Advanced Mode” screens.
It’s not great for portability as it comes (in a car, for example). I have not tried any of the USB to Ethernet adapters with my smartphone or tried a Raspberry Pi as a WiFi to Ethernet bridge. OpenSpot requires an Ethernet cable connection meaning no WiFi though there are plans to add this and uses USB for power and firmware upgrades. As with these devices in DMR mode, they do not transmit a valid call sign. The radio ID is not valid identification. If you listen to a repeater in FM it will ID in CW. Unfortunately, the cost is about twice that of the DV4Mini 182.50 € which, when I ordered, was about $235 including shipping. More: https://www.sharkrf.com/
Other new tech (Christmas gifts?). With advancements in Software-Defined Radios (SDR) I’m seeing a new breed of devices hams can use as radios: your smartphone. Well, at least something that resembles a smartphone or tablet – still need the additional hardware. A device out of the UK called “MyDel Hamfone Smartphone Transceiver” is available. It offers a 3G cellphone, 70cm transceiver (500mw/1W) with camera, expandable SD card, and GPS. The few reviews are positive but there is some question if its FCC certified in the US. More: http://www.hamradio.co.uk/amateur-radio-handheld-radio-mydel-handhelds/mydel/mydel-hamfone-smartphone-transceiver-pd-6093.php
 Bob – W2CYK and the guys over at RFinder (the online repeater directory of the ARRL) have released the “RFinder Android Radio.” Their device integrates 4G LTE & GSM cell technologies alongside FM (DMR is also available) radios into a device with the RFinder repeater directory database. The directory offers coverage maps and switching repeaters is a point-and-click away. They also boast the elimination of codeplugs for DMR. This is great as finding codeplugs, or the information for one, is not always readily available. More: http://androiddmr.com
Bob – W2CYK and the guys over at RFinder (the online repeater directory of the ARRL) have released the “RFinder Android Radio.” Their device integrates 4G LTE & GSM cell technologies alongside FM (DMR is also available) radios into a device with the RFinder repeater directory database. The directory offers coverage maps and switching repeaters is a point-and-click away. They also boast the elimination of codeplugs for DMR. This is great as finding codeplugs, or the information for one, is not always readily available. More: http://androiddmr.com
This past month, the Parma Radio Club invited me to their meeting to give the Raspberry Pi presentation. There was a lot of good discussion and questions. This is always good to hear because you know the audience is engaged, thinking, and ultimately providing real-time feedback on the presentation. Thanks for having me at your meeting. More: http://www.parmaradioclub.com/
Don’t forget, National Parks on the Air will be wrapping up at the end of the year. According to Tom Gallagher – NY2RF, NPOTA is getting closer to #1MillionQSOs: https://twitter.com/hashtag/1millionqsos. Look out for those NPOTA stations to get your score up for your wallpaper (that is certificate if you don’t operate special events and contests).
 Starting this past fall with the kickoff of new TV seasons, the CW is airing a show called “Frequency” loosely based off the 2000 Sci-Fi thriller of the same name. It starred Dennis Quaid and Jim Caviezel as father and son, Frank and John Sullivan. This was big with hams because the movie incorporated something that resembled ham-radio which allowed the father and son to talk 30 years into the past and future. The TV show has gotten positive reviews with a Rotten Tomatoes score of 74% with the biggest criticism being the back-and-forth between now and 20 years in the past. It airs Wednesday nights at 9pm (Ham Nation time so it gets the DVR treatment here) with the last couple episodes available on the CW website and on Netflix streaming. More: http://www.cwtv.com/shows/frequency/
Starting this past fall with the kickoff of new TV seasons, the CW is airing a show called “Frequency” loosely based off the 2000 Sci-Fi thriller of the same name. It starred Dennis Quaid and Jim Caviezel as father and son, Frank and John Sullivan. This was big with hams because the movie incorporated something that resembled ham-radio which allowed the father and son to talk 30 years into the past and future. The TV show has gotten positive reviews with a Rotten Tomatoes score of 74% with the biggest criticism being the back-and-forth between now and 20 years in the past. It airs Wednesday nights at 9pm (Ham Nation time so it gets the DVR treatment here) with the last couple episodes available on the CW website and on Netflix streaming. More: http://www.cwtv.com/shows/frequency/
 Finally, don’t forget the HF Santa Net through Christmas Eve. Starts at 8:30 pm Eastern and can be found on 3916 kHz for the little ones to have a chance to talk with Santa! More: http://www.3916nets.com/santa-net.html
Finally, don’t forget the HF Santa Net through Christmas Eve. Starts at 8:30 pm Eastern and can be found on 3916 kHz for the little ones to have a chance to talk with Santa! More: http://www.3916nets.com/santa-net.html
Thanks for reading. Happy holidays, Merry Christmas, and Happy New Year!
73… de Jeff – K8JTK